VELOTIX USE CASE
Database Activity Monitoring
As part of managing the entire data security lifecycle, Velotix collects, consolidates and analyzes activity logs from managed databases.
Unlock Rich Insights with Velotix Post-Processing
Velotix performs various types of post-processing on database activity logs, in order to enable a rich set of insights and actions:
- Database activity log collection
- Correlation of activity logs with user and database attributes
- Correlation of activity logs with approved requests in Velotix, to see who approved the access for each performed query
- Analysis and aggregation of database activity by user/data attributes to show activity and surface anomalies in various dimensions
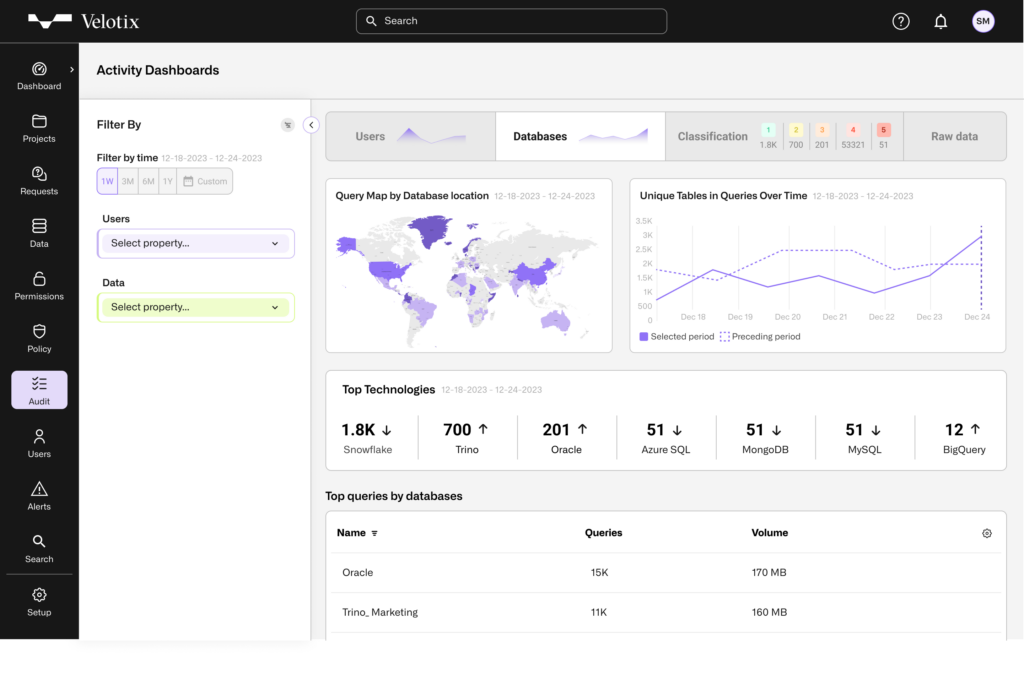
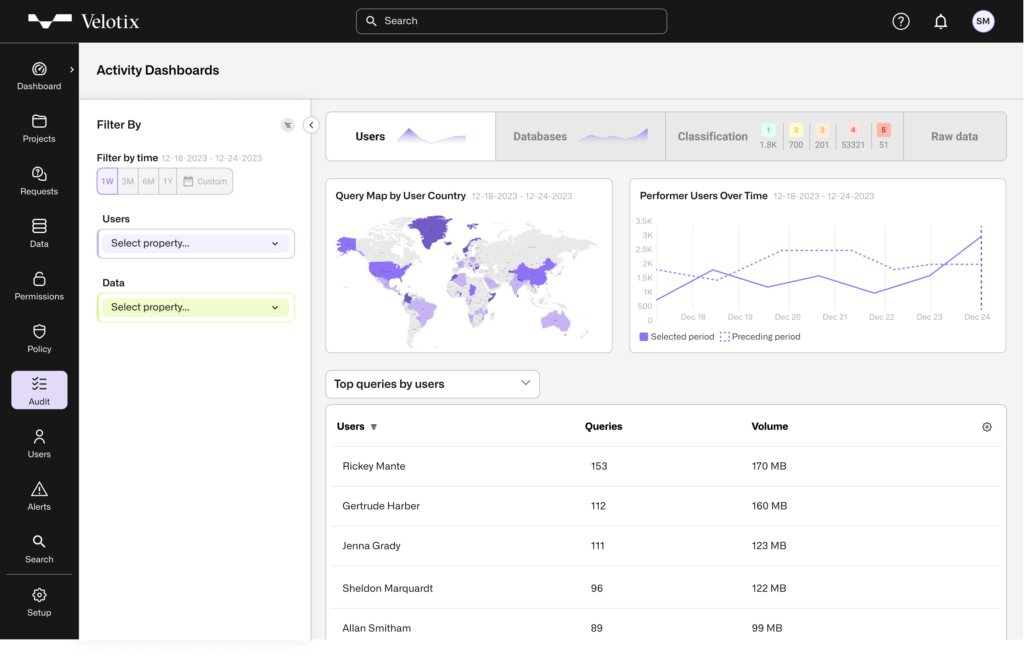
Enhance Data Security with Comprehensive Monitoring
Velotix database activity monitoring complements traditional data access management and permission management by correlation actual usage of data to granted permissions, enabling users to gain various types of insights, like:
- Understand which permissions are not being used and not follow-up on removing them in order to reduce the attack surface for databases
- Gain insight into usage patterns and identify anomalies, enabling organizations to identify suspicious activities performed by outsider actors using compromised credentials
- Apply all kinds of filter on activity logs, in order to understand usage patterns by geography, department or any other user attribute
Book Your Free Demo
See how Velotix can help you gain control of your data security and compliance.
