Velotix for Information Security Leaders
Turn Security from Gatekeeper into Scale Enabler
Drive secure data democratization without the drama.
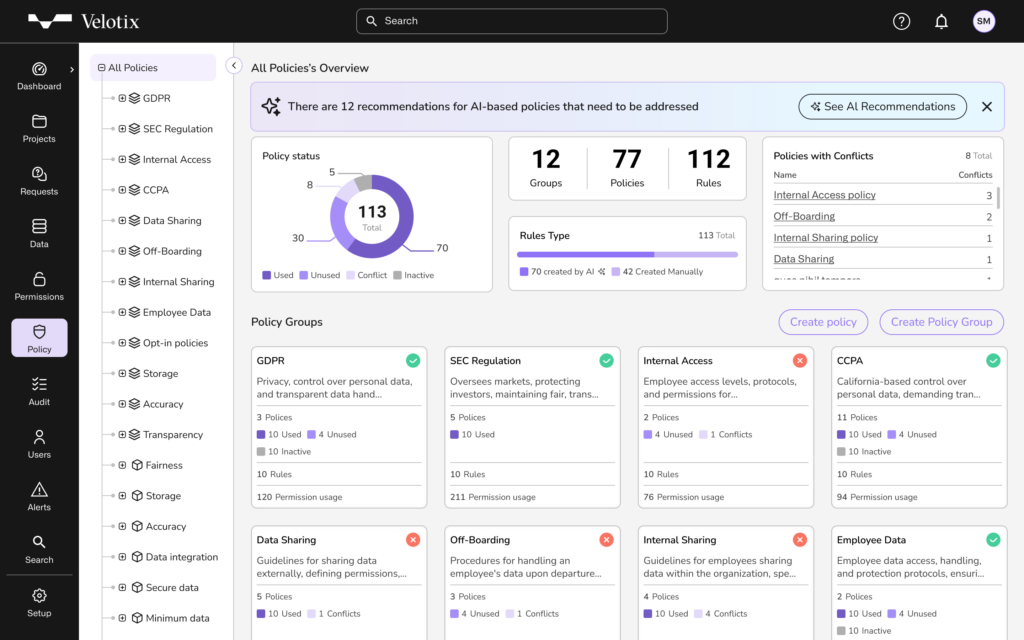
Get Complete Visibility with a Data Security Control Tower
In today’s digital landscape, detecting breaches after they occur is a headline that never tires. Velotix proactively monitors for data that goes off-grid and permissions that conflict with data protection policies or activity. With Database Activity Monitoring (DAM) and Joiner Mover Leaver (JML) automation, any changes prompt an alert and recommends a path to reconciliation, allowing your team to respond quickly and decisively.
- Challenge: Limited visibility to change leave gaps.
- Solution: With DAM and JML automation, Velotix instantly alerts on changes, guiding your team with actionable insights for swift resolution.
- Challenge: Dark data and inaccurate permissions leak data off grid and into the wrong hands.
- Solution: Velotix uses AI to continuously monitor access patterns, delivering real-time alerts for quick remediation.
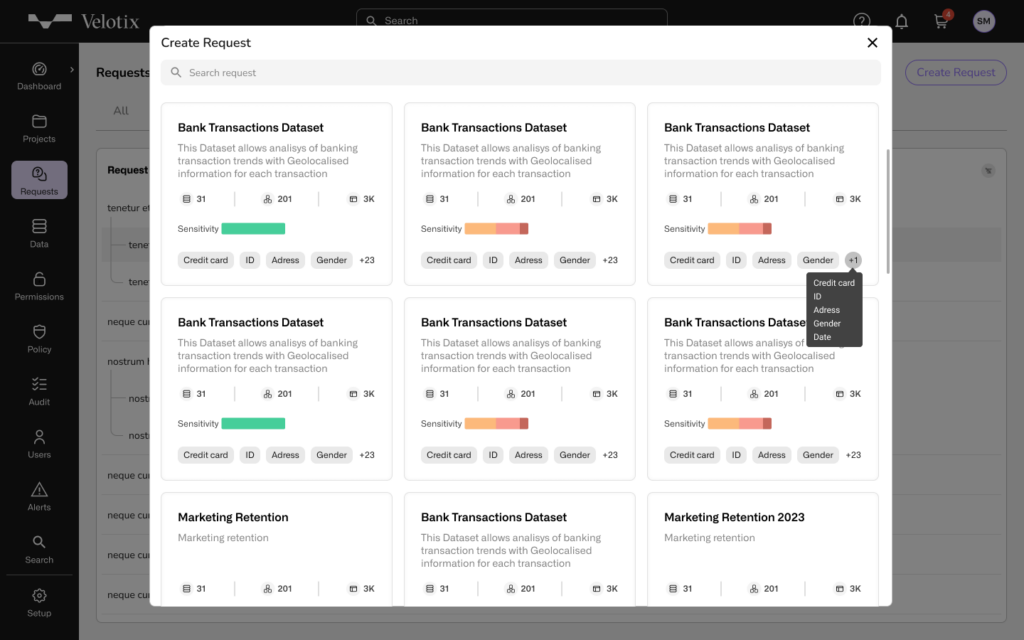
Gain Control with Granular Access Permissions
Broad permissions lead to risk. Velotix’s fine-grained access controls protect sensitive data by aligning access with user roles and data sensitivity, reducing the risk of unauthorized access. From encryption to detailed access permissions, Velotix ensures that only the right people access the right data, reinforcing compliance and data security across the board.
- Challenge: Overly broad permissions expose data to unnecessary risk.
- Solution: Velotix enforces granular access, limiting exposure by setting permissions precisely based on role and data sensitivity.
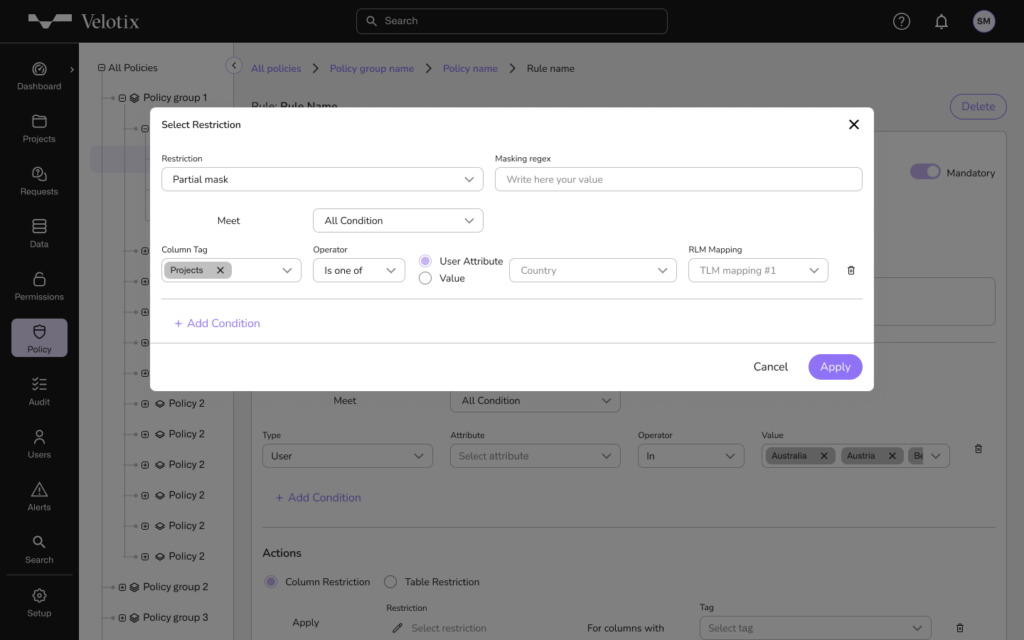
Automate Data Privacy with Dynamic Privacy Enhancing Technologies (PETs)
Securing data during processing is critical yet often overlooked. Velotix’s dynamic privacy enhancing technologies—such as masking, pseudonymization, and encryption—protect sensitive data even as it’s used across workflows, preserving privacy without hindering data utility. Velotix ensures that sensitive data stays secure while remaining accessible to those who need it.
- Challenge: Traditional data protection methods leave data vulnerable during processing.
- Solution: Velotix’s PETs transform sensitive data into protected formats across any pipeline, securing privacy without limiting utility.
See Velotix in Action
Get hands-on with real-time data protection at scale.
